Hello everyone!
In this article, I'll introduce the trending concept of Continuous Threat Exposure Management (CTEM) through the noteworthy product, XM Cyber. This is the first installment, focusing on an overview of CTEM and XM Cyber.
Key Points of This Article
✓ CTEM is a new security trend proposed by Gartner.
✓ XM Cyber is gaining attention as a key player in implementing CTEM.
✓ XM Cyber excels in the area of Attack Path Management (APM)
CTEM
Continuous Threat Exposure Management (CTEM) refers to the processes and frameworks organizations use for ongoing monitoring and management of cyber threats. Its primary goal is to strengthen security by continuously monitoring devices and SaaS services that could be potential targets for attacks.
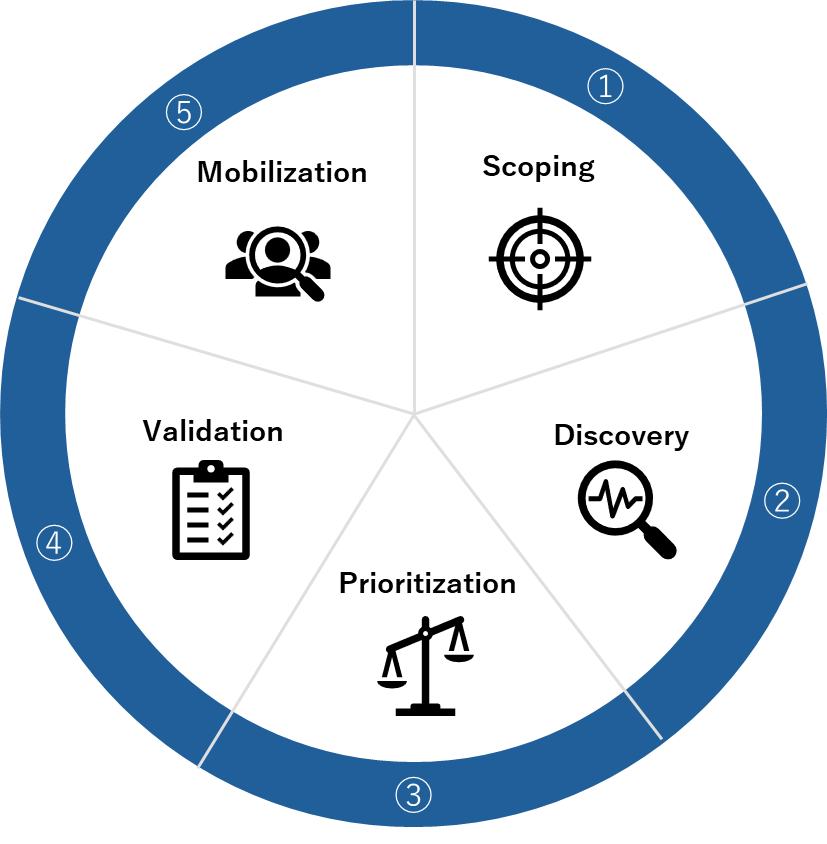
CTEM consists of five key steps:
1. Scoping:Identify the areas at risk from the organization's sites and cloud services.
2. Discovery:Locate the assets within those targeted areas.
3. Prioritization:Rank the discovered assets based on risk.
4. Validation:Verify whether the prioritized assets are actually attackable.
5. Mobilization:Mobilize personnel to address vulnerabilities and evaluate risks.
By iterating through these steps, organizations can identify risks and develop responses to attacks, thereby enhancing their resilience against threats and strengthening overall cybersecurity.
This is the the fundamental concept of CTEM.
XM Cyber
A notable player in the CTEM space is XM Cyber. Let's look at the company overview:
・ Founded in 2016 in Israel
〜Developing products using cutting-edge technology and attack methodologies.〜
・ Acquired by the Schwarz Group in 2021
〜Improving quality and customer experience based on feedback from a manufacturing powerhouse.〜
・ Operating in Europe, the US, Asia, and Japan
For more details, please visit their official website:https://xmcyber.com/
XM Cyber's Position in the Security Domain (CTEM)
As CTEM is a new trend, it's important to understand XM Cyber's role within the broader security landscape.
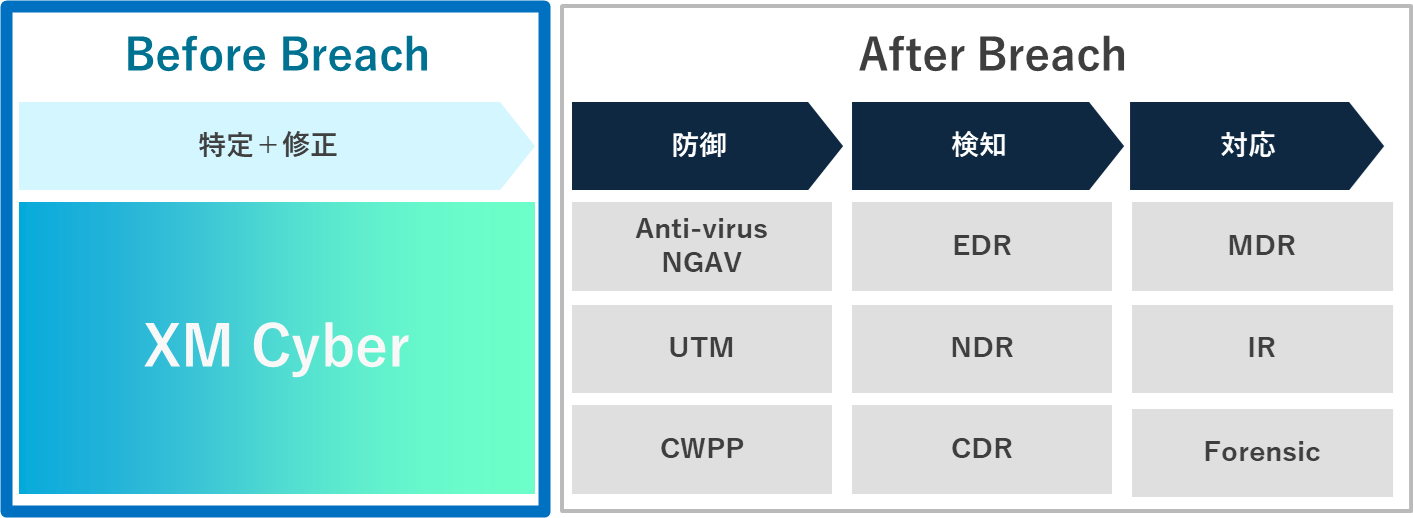
EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) have gradually become standard security measures. The current focus is on how quickly organizations can respond after an intruder has breached their defenses, emphasizing the "After Breach" aspect.
In contrast, XM Cyber (CTEM) focuses on "Before Breach" measures. By identifying external assets that are exposed to potential threats and internal endpoints that could facilitate lateral movement, organizations can implement proactive measures to prevent attacks.
APM
Attack Path Management (APM) is a crucial component of CTEM. Since XM Cyber emerged from an ATP (Automated Threat Protection) background, it excels in this domain. Here's an overview:
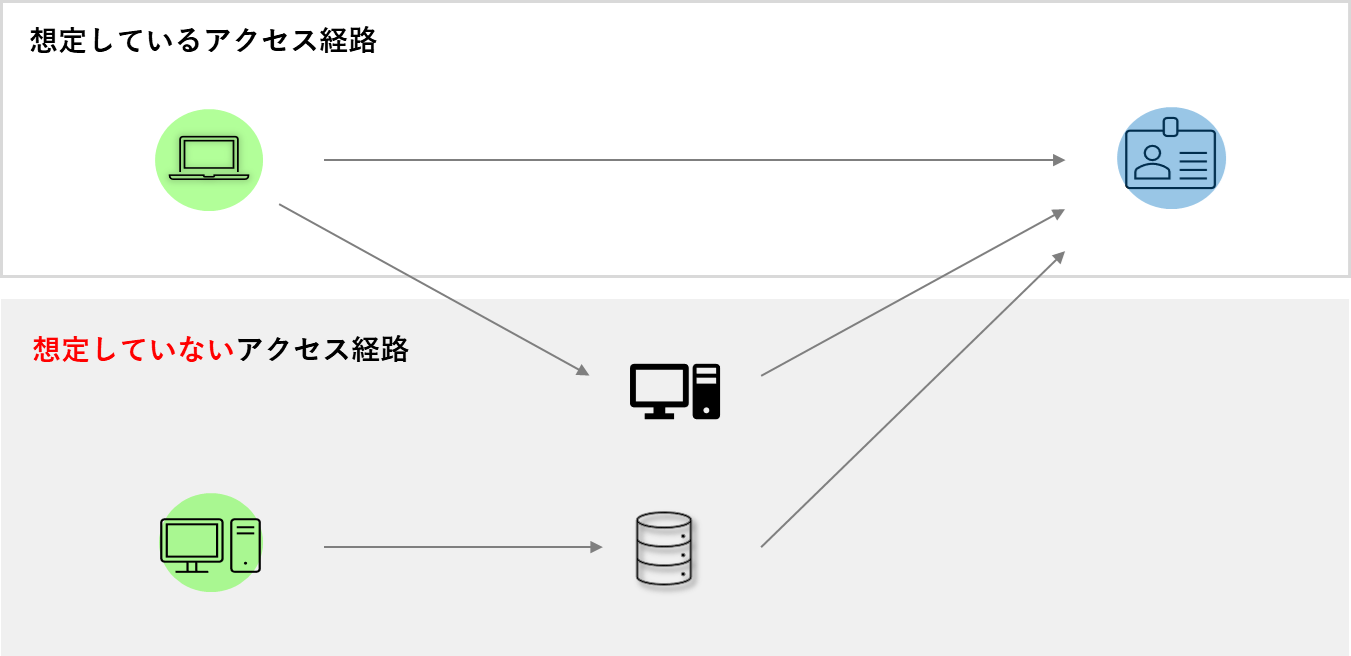
The concept of attack paths may seem complex, but consider how many credentials your PC has and which cloud services or company assets it can access. While many organizations have policies in place, they often lack the means to verify actual access capabilities.This is the purpose of APM (Attack Path Management).
XM Cyber's advantage lies in its method for discovering attack paths. By using an agent on PCs and integrating with cloud services through APIs, XM Cyber can recreate users' environments in its cloud. This enables continuous monitoring without impacting the actual environment, thus establishing an ideal CTEM framework!
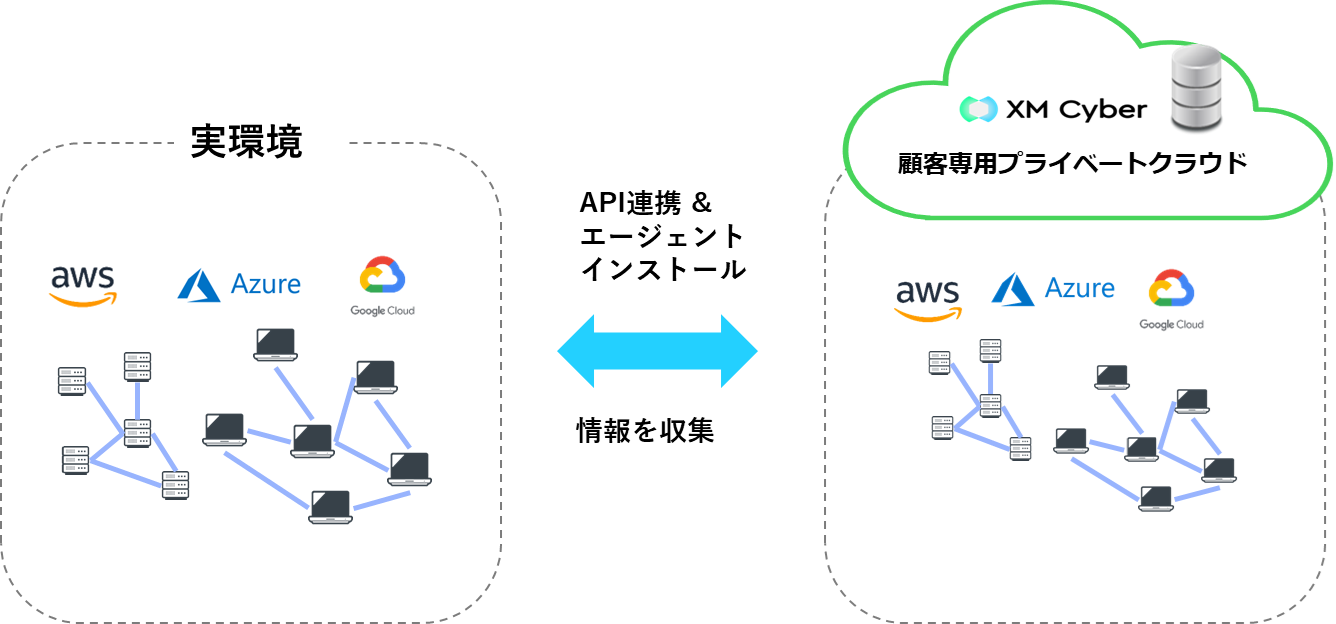
XM Cyber's advantage lies in its method for discovering attack paths. By using an agent on PCs and integrating with cloud services through APIs, XM Cyber can recreate users' environments in its cloud. This enables continuous monitoring without impacting the actual environment, thus establishing an ideal CTEM framework!
Thank you for reading!
In this article, we introduced CTEM and XM Cyber. In the next article, we will delve into specific product screens to demonstrate how to implement CTEM. Stay tuned!
Note: The information in this blog is current as of the publication date. As updates occur, we cannot guarantee the accuracy, timeliness, or completeness of the information.
他のおすすめ記事はこちら
著者紹介

SB C&S株式会社
技術本部 技術統括部 第4技術部 1課
秋池 幹直