Hello everyone!
In this article, titled "Discover CTEM through XM Cyber," we will explore the trending concept of Continuous Threat Exposure Management (CTEM) using the notable product, XM Cyber.
This time, we'll examine how XM Cyber fits into the CTEM framework by looking at actual screens and detection results.
Recap from Last Time
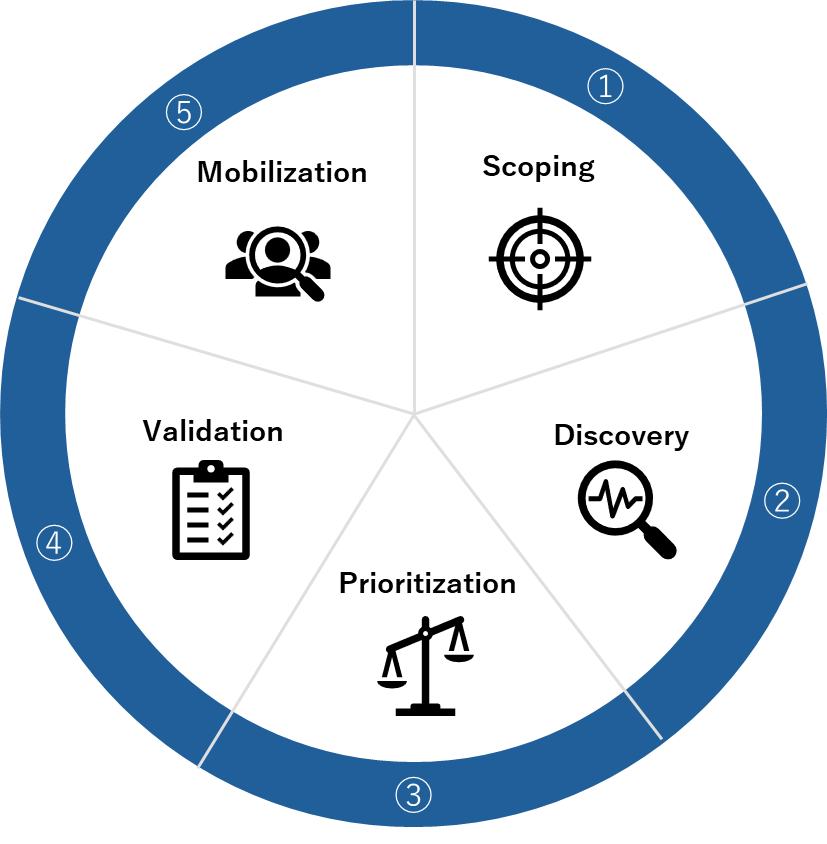
CTEM consists of five key steps:
1. Scoping: Narrowing down the areas that are potential targets from the organization's sites and cloud services.
2. Discover: Identifying the assets within those targeted areas.
3. Prioritization: Ranking the identified assets based on risk.
4. Validation: Verifying whether the prioritized assets are actually vulnerable to attacks.
5. Mobilization: Mobilizing personnel to address vulnerabilities and evaluate risks.
This time, I'll explore how to implement these steps using XM Cyber!
1.Scoping
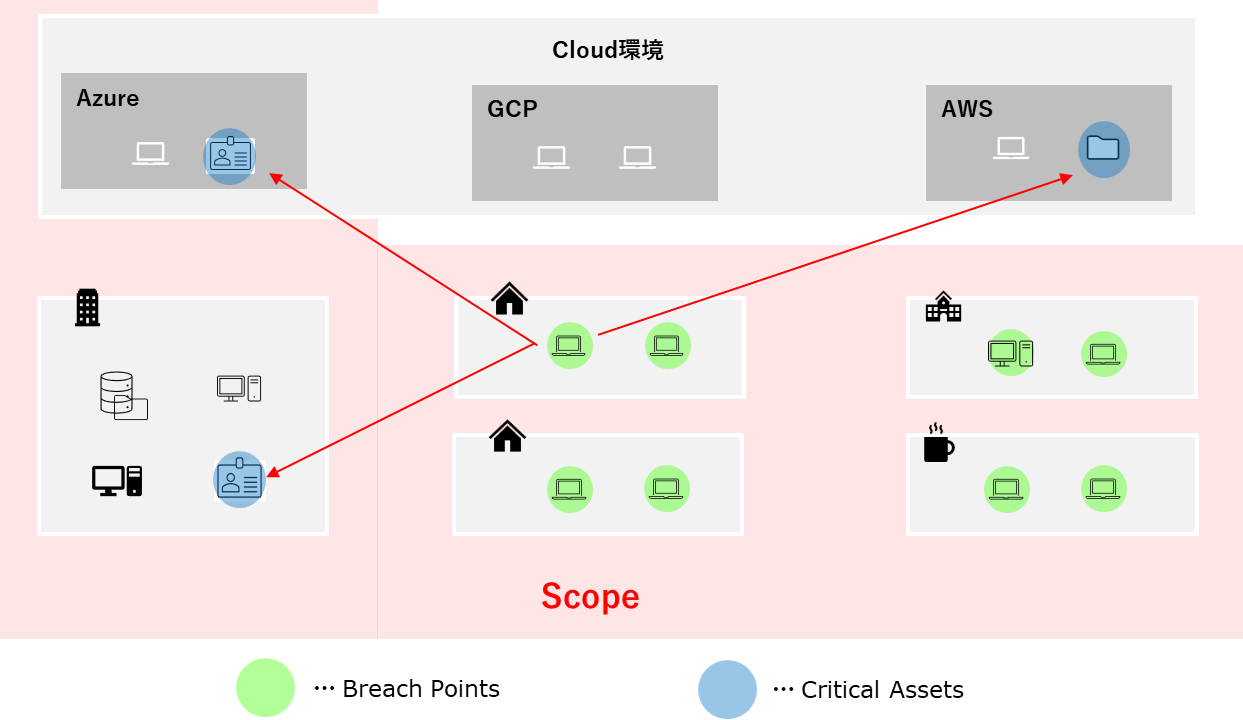
First, I narrow down the areas that could be targeted based on the organization's sites and cloud services. This involves taking an inventory of the assets owned by the organization or company.
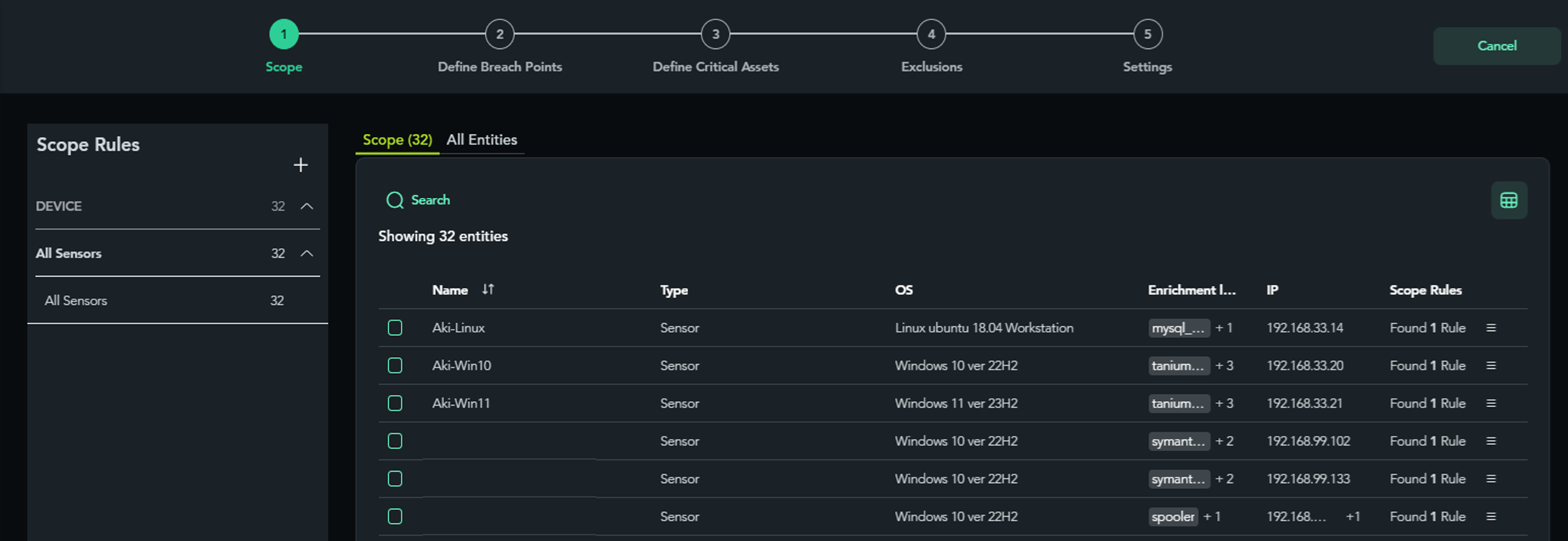
In XM Cyber, Scoping is performed during the scenario creation process. A scenario involves simulating a cyber attack by defining the attack targets (Scope), breach points, and critical assets, leading up to a virtual attack. While this may seem complex, it essentially involves selecting entry points where a breach could occur and identifying sensitive servers or file storage containing critical information.
Here's what the actual scenario creation screen looks like. The Scope is set to include all devices with the agent installed.
Tags for asset attributes, referred to as Entities, allow for flexible scenario creation. We will discuss the creation of scenarios tailored to Entities and objectives in a future article!
2.Discover
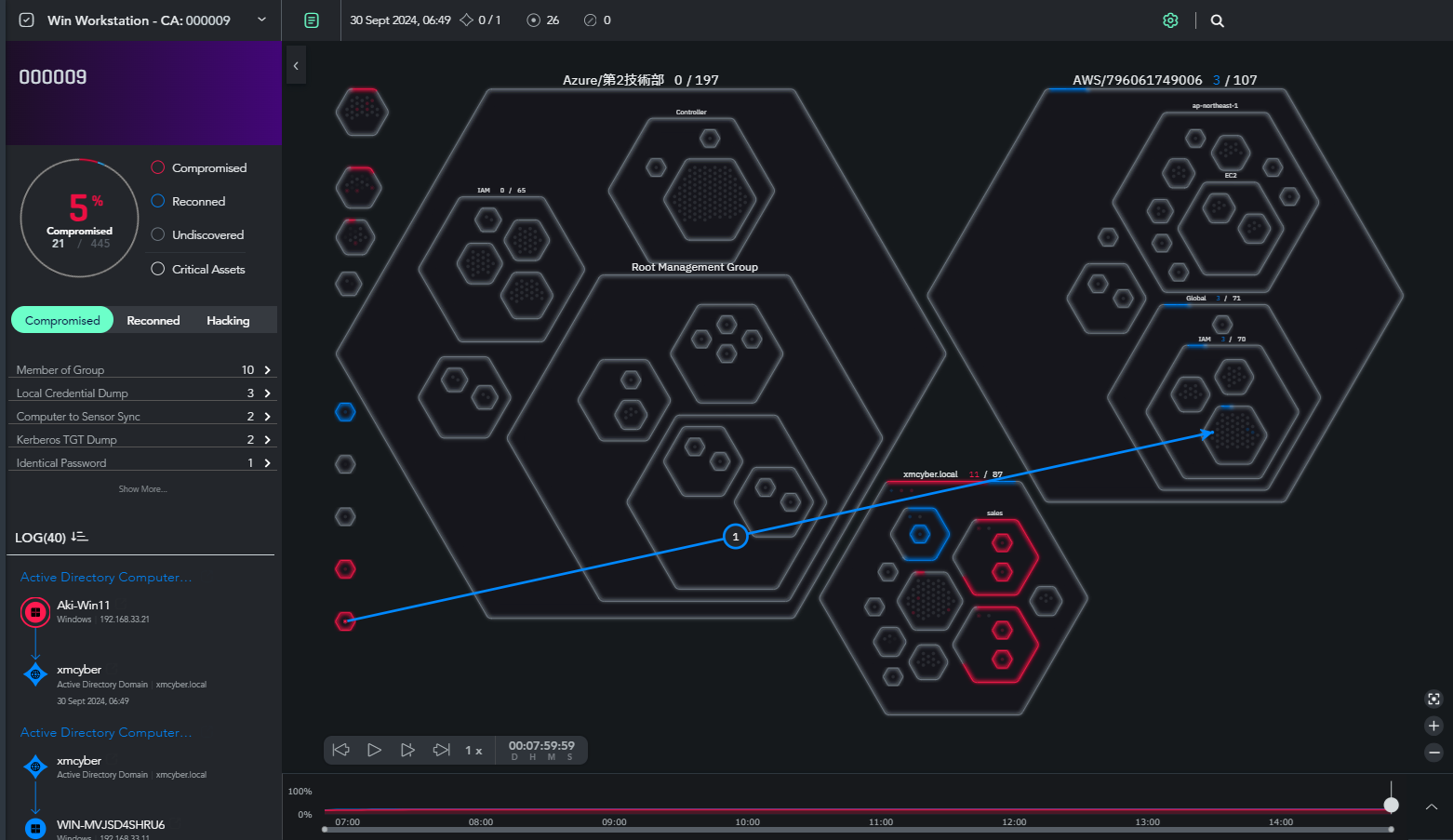
In the Discover phase, we identify the assets present in the targeted areas. This involves checking for misconfigurations and vulnerabilities in both on-premises and cloud environments. In XM Cyber, you can review the assets included in the Scope, whether they are vulnerable to breaches, and the access paths that could be used for attacks through a page called Battleground.
Below is an actual view of the Battleground. The assets in the verification environment, including Azure, AWS, AD domains, and external PCs, are grouped in hexagons. The red icons indicate compromised assets, showing that an attack path has been established to the assets on AWS.
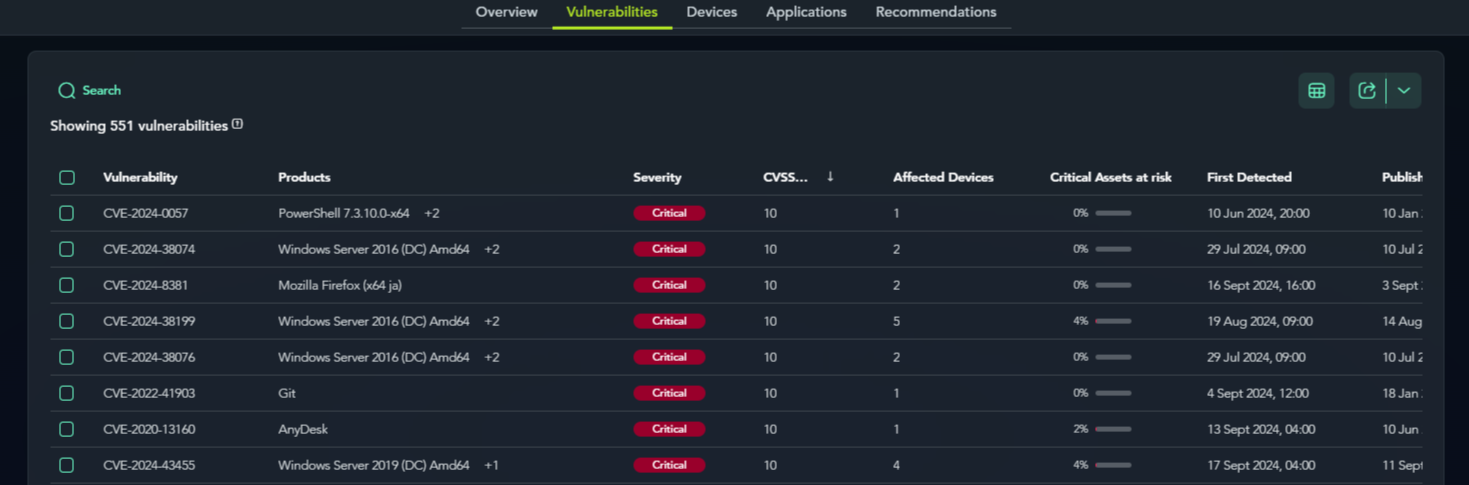
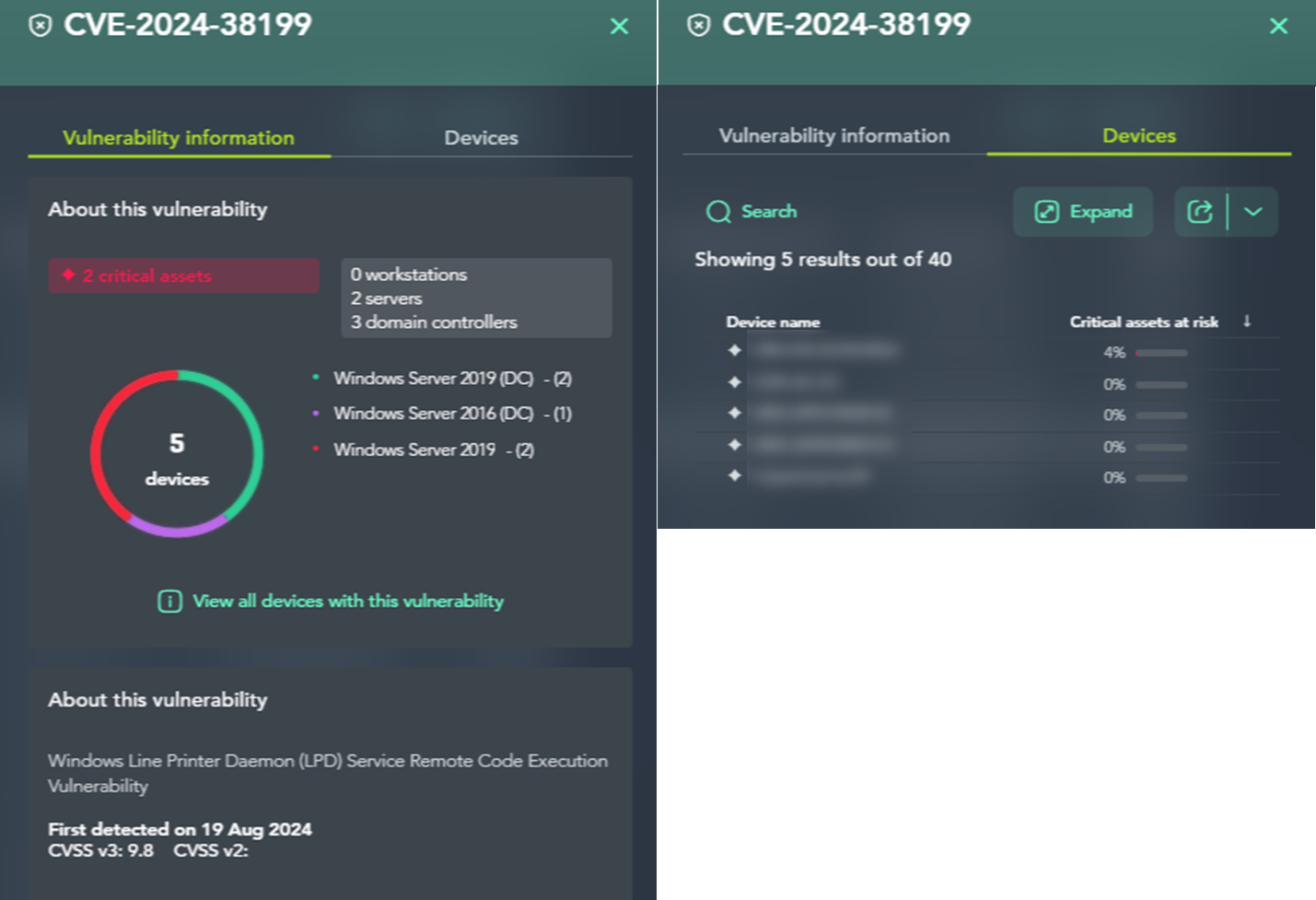
Vulnerabilities hidden within the assets are listed, providing an overview of CVEs, remediation methods, and the affected devices.
3.Prioritization
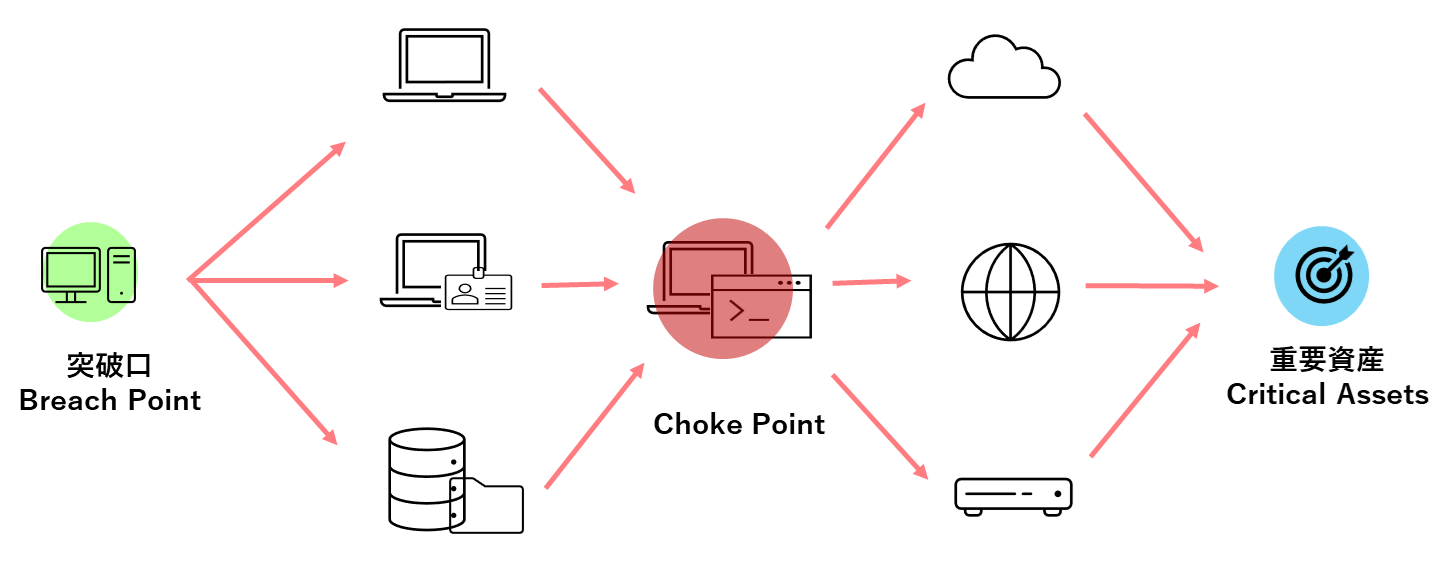
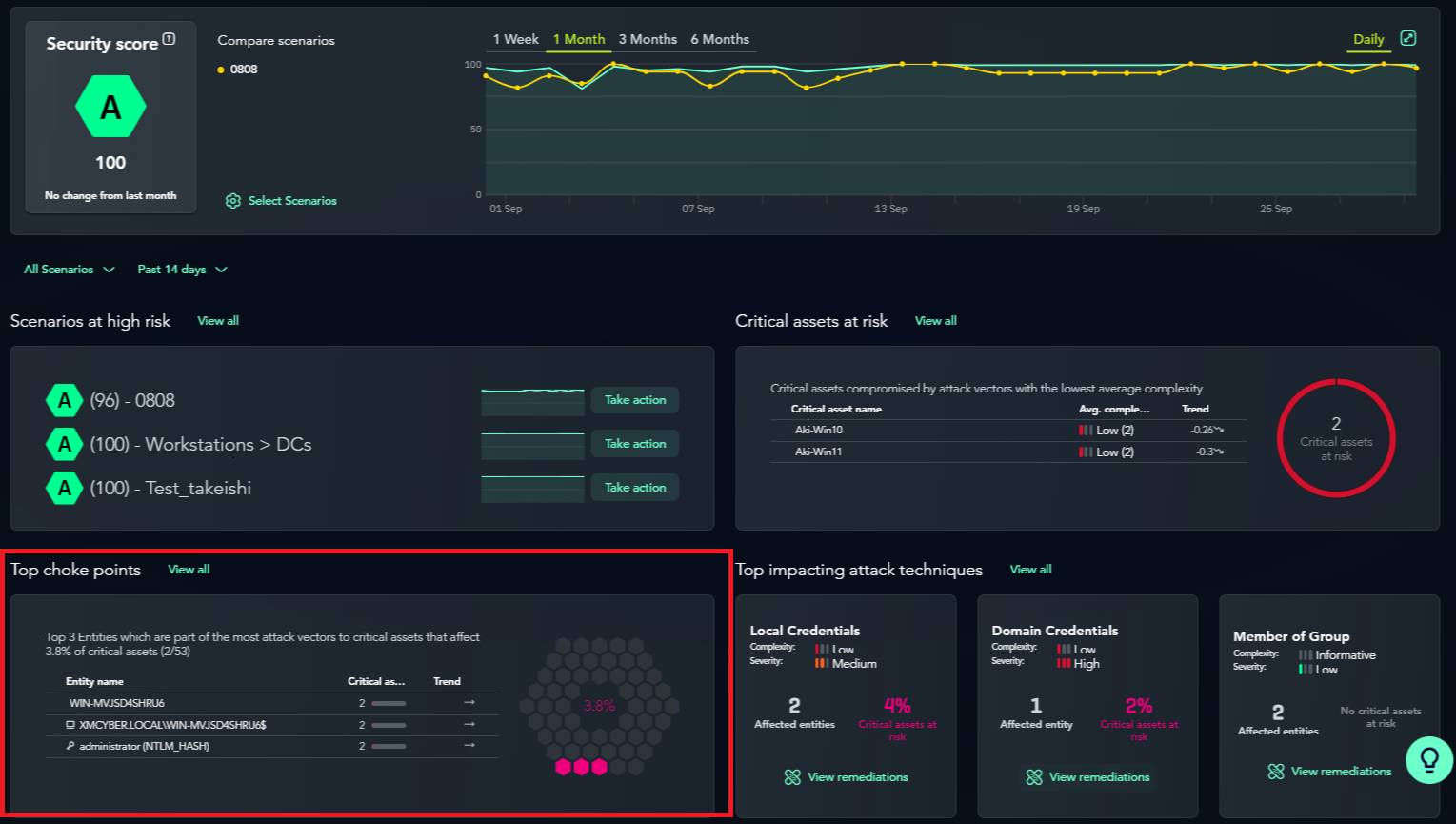
In the Prioritization phase, we rank the identified assets. It is crucial to prioritize the important assets and recognize points referred to as "Choke Points," where multiple attack paths intersect.
The "Choke Points" are clearly visible on the dashboard.
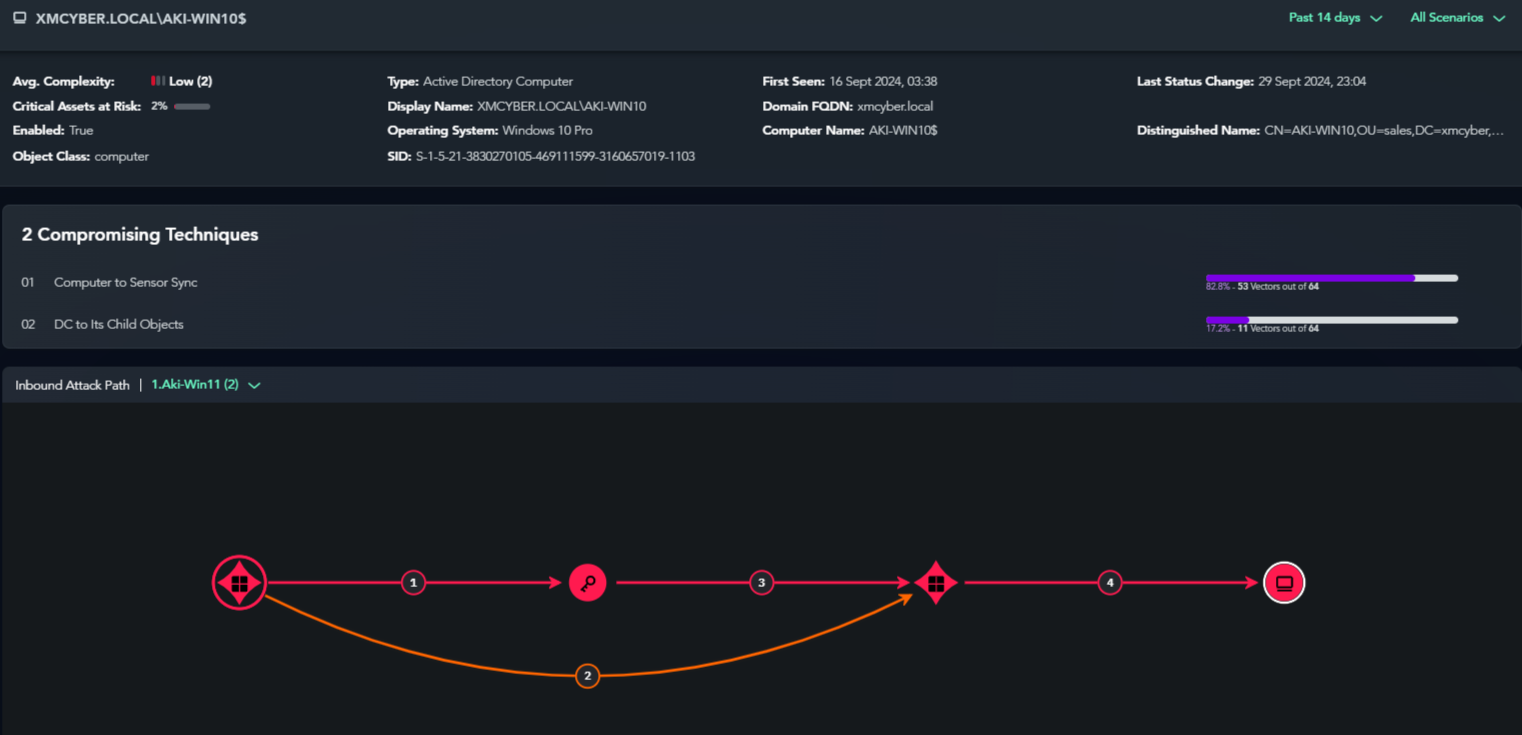
Devices that are Choke Points exist on multiple attack paths.
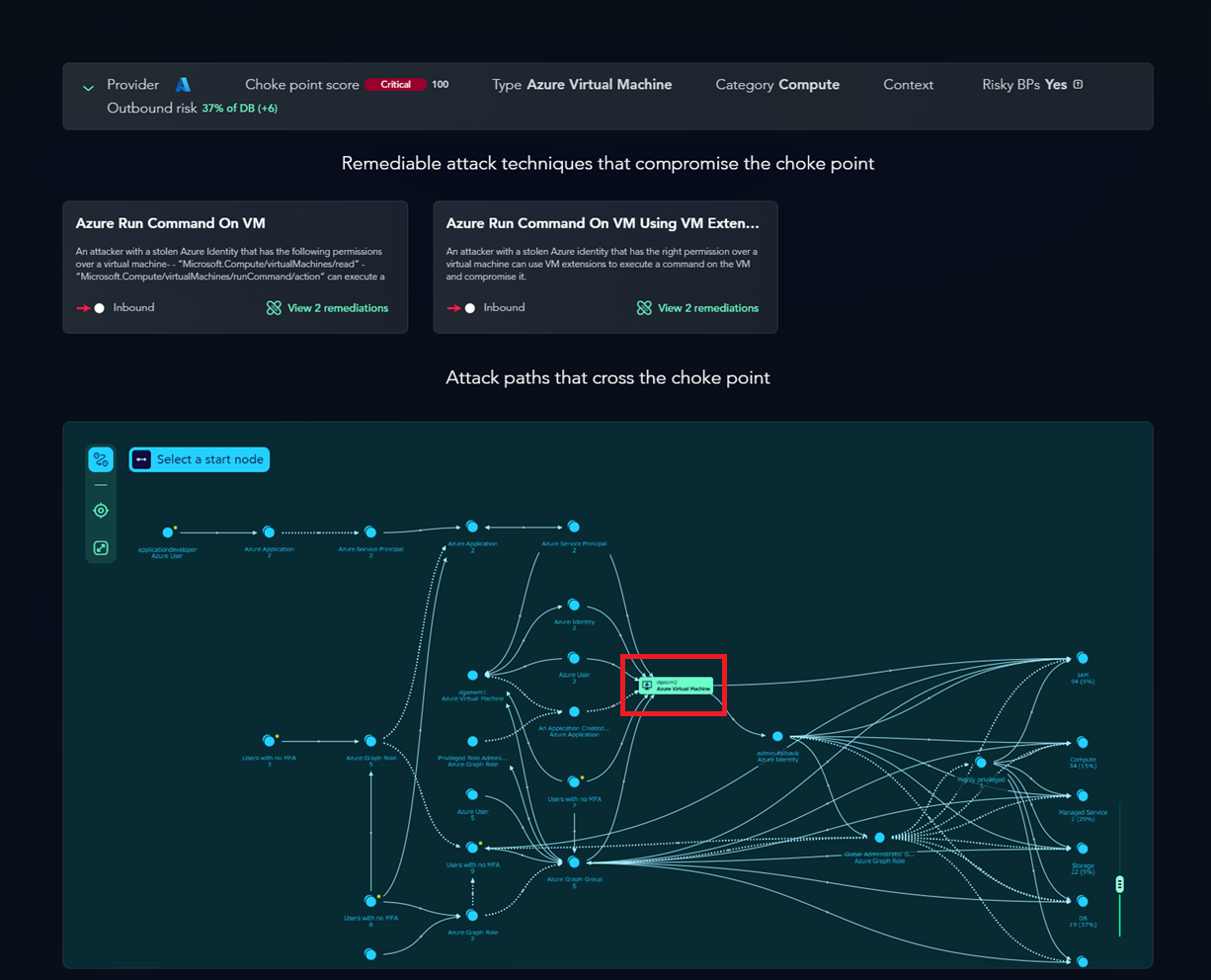
The same applies to cloud assets; once attack paths are visualized, it becomes immediately apparent.
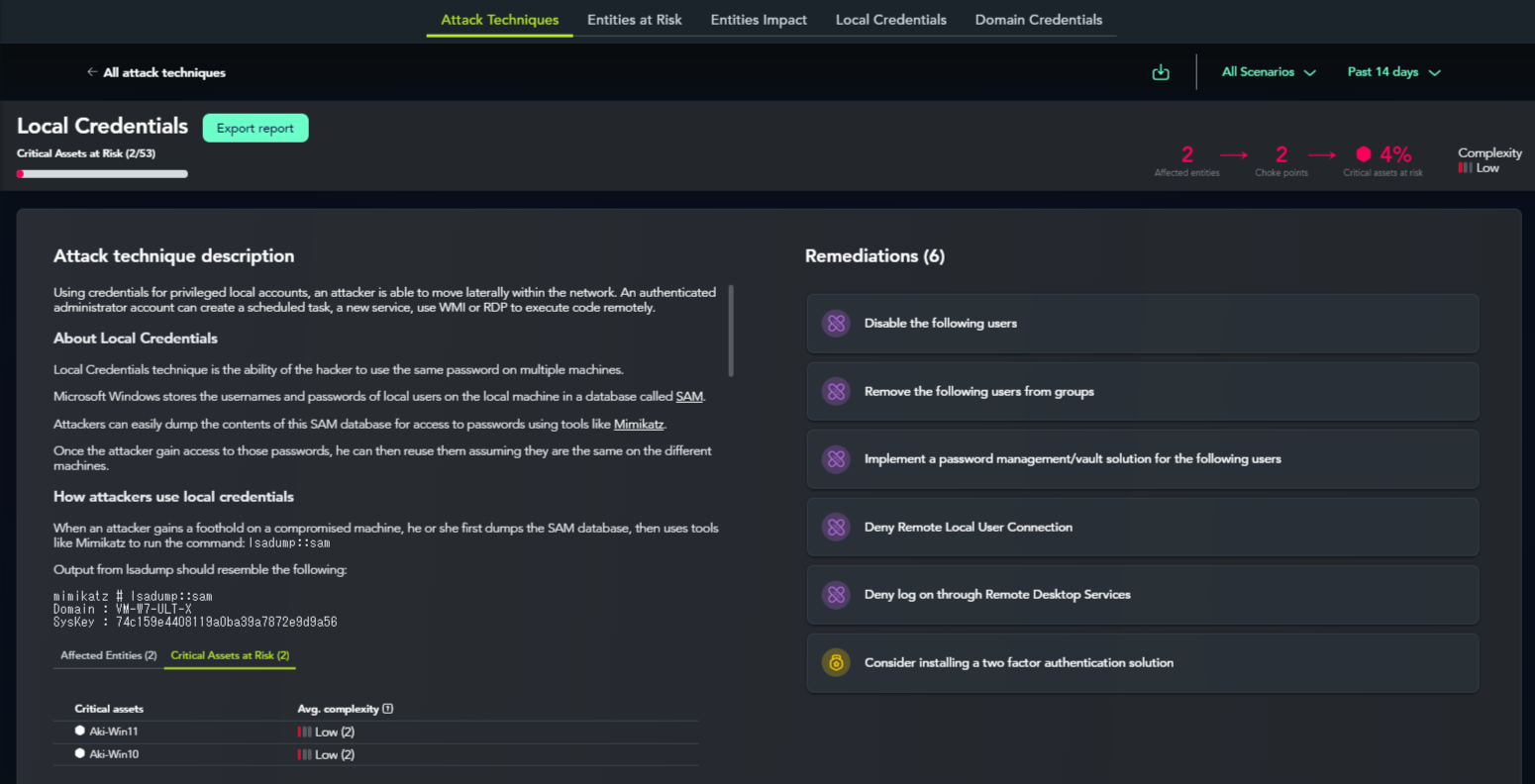
4.Validation
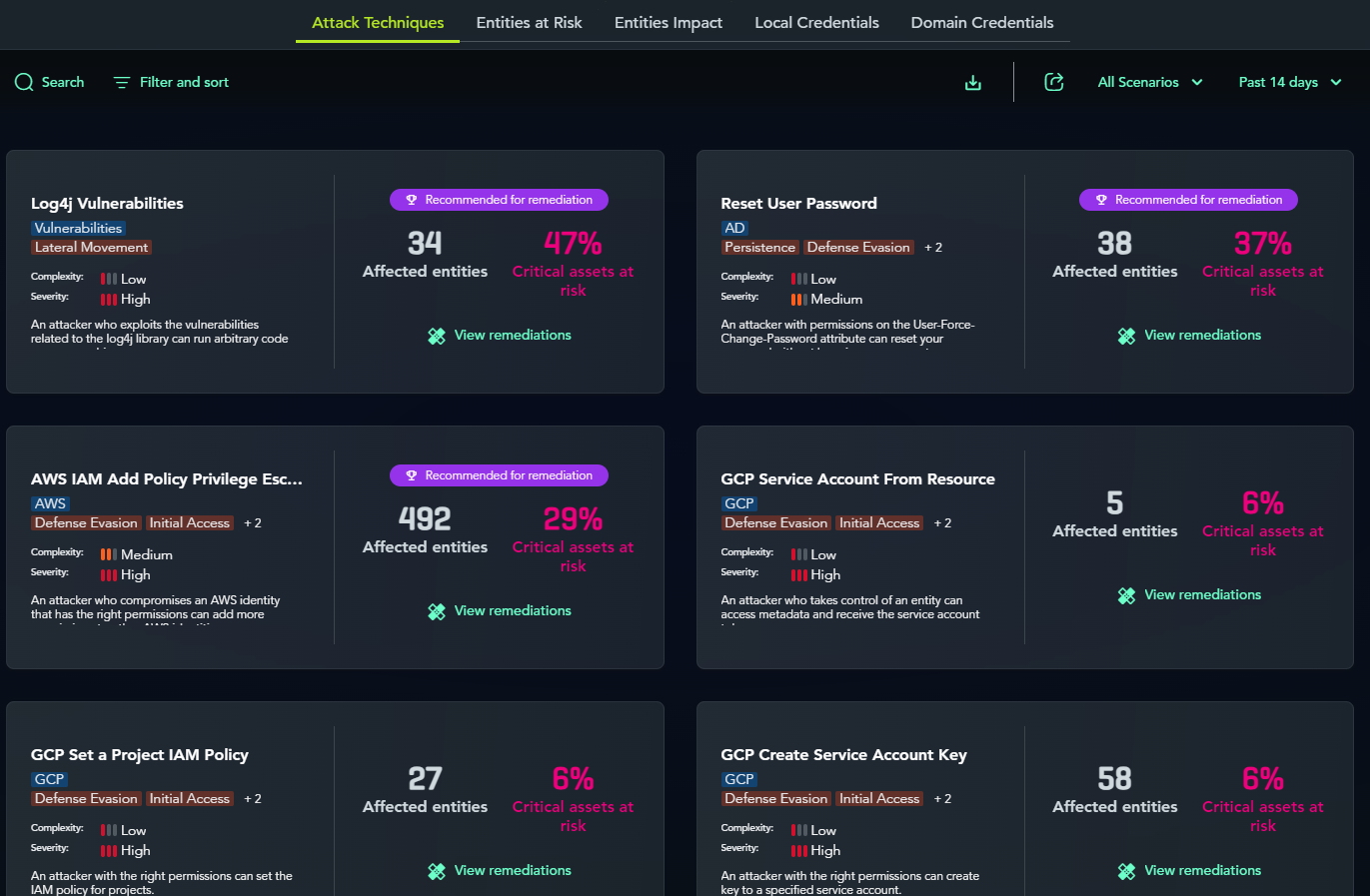
Validation involves checking whether the prioritized assets are actually vulnerable to attacks. XM Cyber allows you to review attack techniques verified in a virtual environment.
n the Attack Techniques detail view, you can see which assets were targeted, descriptions of the attack methods, and remediation strategies.
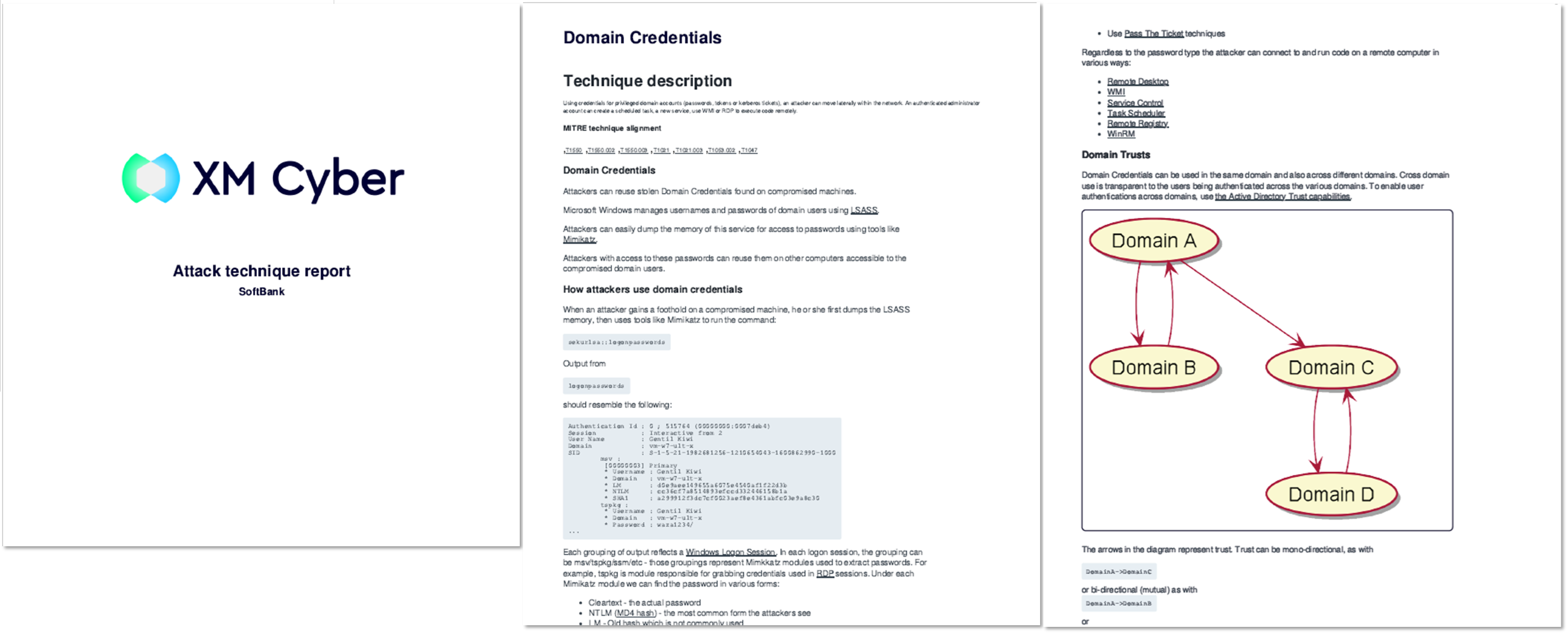
The "Attack technique description" provides detailed information, including an overview of how attackers might exploit the technique, prerequisites, and associated MITRE ATT&CK® techniques.
Here are the MITRE ATT&CK® techniques detected in this example:
T1021
T1021.001
T1550.002
T1550.002
T1550.003
T1021
T1021.003
T1053
T1047
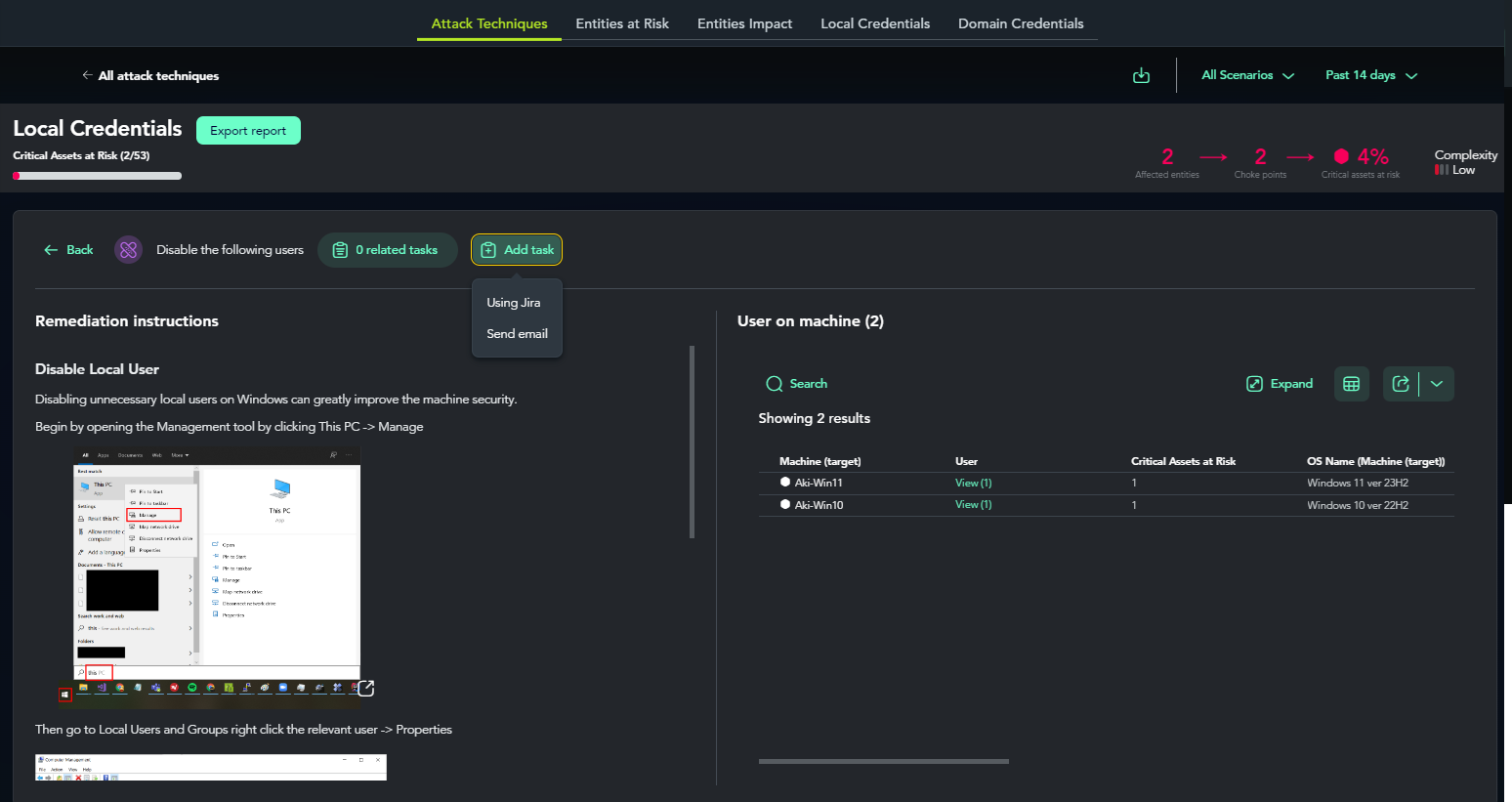
5.Mobilization
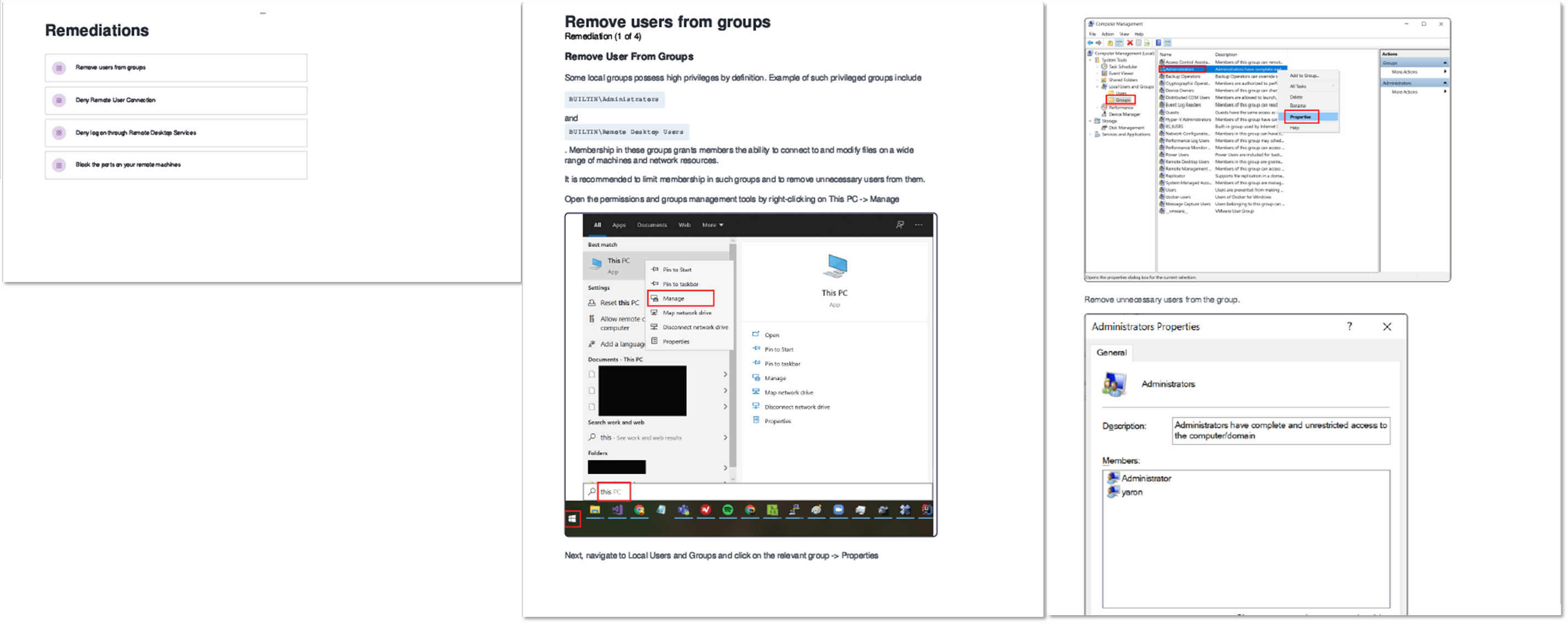
In the Mobilization phase, personnel are mobilized to address vulnerabilities and assess risks. From the previous Attack Techniques screen, you can integrate with ticket management services and send emails to response teams.
Additionally, a reporting feature is implemented for generating reports.
Thank you for reading! By using XM Cyber, you can comprehensively cover CTEM. This article focused on introducing screens aligned with the CTEM framework, but we plan to publish product introductions based on use cases in future articles. Please stay tuned!
Note: The content of this blog reflects information as of the publication date. As updates occur, we cannot guarantee accuracy, timeliness, or completeness.
他のおすすめ記事はこちら
著者紹介

SB C&S株式会社
技術本部 技術統括部 第4技術部 1課
秋池 幹直